RC DARK Tool V1.2.3 Latest Version
Introduction
The RC DARK Tool V1.2.3 is a remote administration tool (RAT) that has gained attention in cybersecurity circles often associated with penetration testing ethical hacking and unfortunately malicious cyber activities. This software allows users to remotely control systems execute commands and manage files making it a powerful utility for IT administrators—but also a potential weapon in the hands of threat actors. While some versions of such tools are used legally for network diagnostics and security research unauthorized deployment can lead to serious legal consequences.
Get This Tool: Click Here
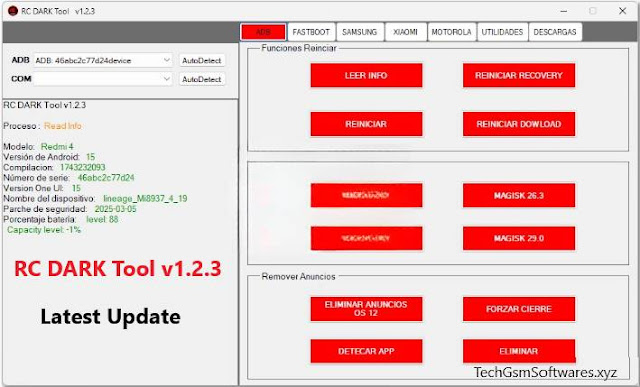
Features of RC DARK Tool:
- IMEI Generator (With dual SIM support)
- OEM Info Editor for PayJoy and Claro devices
- FRP Key Unlock (Fast boot Mode)
- Disable System Updates for Samsung & Xiaomi
- Remove Ads (OS 12 Supported)
- Install Magisk 26.3
- Fast boot & ADB support for various functions
- App Manager for system and user apps
- QCN Backup (Diag Mode)
- Bootloader Unlock (Fast boot)
Read Also: ADB MDM Fix Tool Latest Update
How To Use?
- First you need to download the zip file by Click Here
- Next you can unzip all files at c: drive (important)
- Ensure you have disabled the antivirus before running the installation
- Next open the folder and install the setup file with some basic instruction
- Run the RC DARK Tool V1.2.3 Latest Update
- you can install all drivers if you already installed skip this step
- Connect the phone and try to do any function
- Enjoy !!!
Conclusion:
The RC DARK Tool V1.2.3 represents a double-edged sword in the realm of cybersecurity—capable of serving as a legitimate remote administration utility for IT professionals while also posing significant risks when misused for unauthorized access. Its functionalities which include remote control file management, and command execution make it comparable to other well-known RATs like Dark Comet and NjRAT though its exact origins and development remain ambiguous. Ethical concerns and legal ramifications surround its use, as deploying such tools without permission violates cybersecurity laws in many jurisdictions.